The NIST cybersecurity framework is comprised of three main components:
- The Core
- Implementation Tiers
- Profiles
In this post we will be focusing on component #1, the core.
Table of Contents
What is the framework core?
The core is a set of cybersecurity activities and outcomes designed to be intuitive and facilitate communication between multidisciplinary teams. The framework core achieves this outcome by organizing activities and outcomes into categories, aligning the categories to informative reference material, and using simple and non-technical language that's easily understood.
Like the NIST Cybersecurity Framework, the Framework Core is made up of three parts:
NIST Cybersecurity Framework Core: Functions
The core functions are broken down into five high level functions that apply to cybersecurity risk management as well as risk management in general.
The five core functions are: Identify, Protect, Detect, Respond, and Recover.
NIST Cybersecurity Framework Core: Categories
One level down from the five functions things get more granular being broken up into 23 categories. These categories were thoughtfully designed to strike a balance between providing a comprehensive breadth of cybersecurity objectives for an organization while not being excessively detailed. Topics covered span cyber, physical, and personnel, with a focus on business outcomes.
NIST Cybersecurity Framework Core: Subcategories
The deepest level of abstraction in the core is the subcategories, all 108 of them. These subcategories are outcome-driven statements designed to enable an organization to implement based on their unique needs. The framework is outcome driven, it doesn't care so much about how an organization achieves its results, it just cares that an organization considers the right variables while creating or improving their cybersecurity program.
For an understanding of how the NIST Cybersecurity Framework Core all comes together, see the chart below:
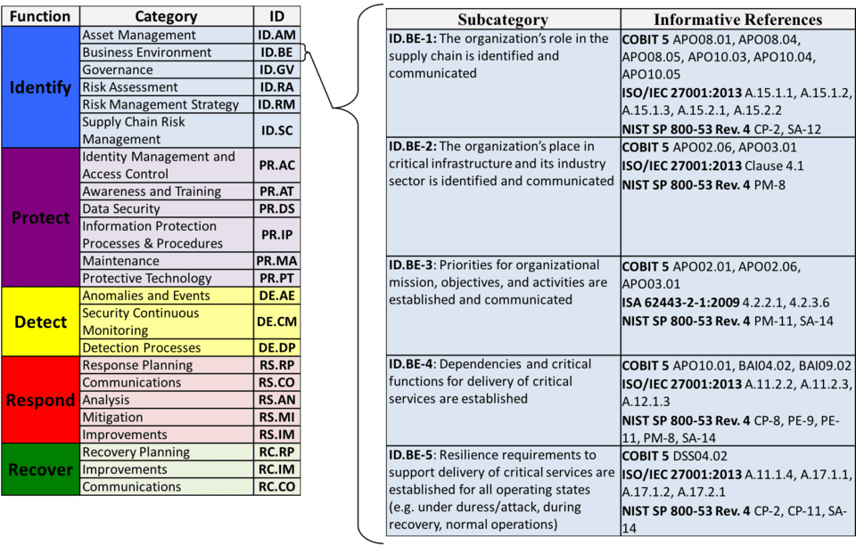
source: NIST
These three components of the core work in harmony to aid an organization in expressing its management of cybersecurity risk by organizing information, enabling risk management decisions, addressing threats, and improving by learning from previous activities.
The Functions align with existing methodologies for incident management and help show the impact of investments in cybersecurity. As you've seen, each of these functions has associated key categories, subcategories, and informative references.
How Do I Use the NIST Cybersecurity Framework Core?
For illustrative purposes, you may have encryption software installed on your mobile devices; it corresponds to the Protect function, specifically the Data Security Category, and PR.DS-1 Subcategory, Data-at-rest is protected. You can weigh the risk of device theft or loss against the chance an employee may lose a cell phone.
The Framework Core provides so much guidance! Data Security, under Protect, is defined for you as “Information and records (data) are managed consistent with the organization’s risk strategy to protect the confidentiality, integrity, and availability of information.” Do your employees have work email on their cell phones or tablets? Has anyone lost an asset with work-related information on it?
As well, NIST compiled a list (not exhaustive, but quite thorough) of Informative References to further assist you to decide how best to accomplish your goals, and how those goals may be impacted by existing requirement or recommendations, depending on your sector or industry.
Further Reading:
