Every now and then, an email with an enticing subject line appears in your inbox and you end up clicking on it, either out of curiosity or because you believe the sender is trustworthy. Sadly, this is how most cyberattacks tend to begin – with a single click. What unfolds next only puts your security and the security of your business in grave danger.
Whether you clicked on a link or the unsubscribe button in the email, you would have potentially opened the floodgates to the possibility of a single or multiple cyberattacks that could hold your business’ future hostage. According to ProofPoint’s Human Factor 2019 report, more than 99 percent of cyberattacks require human interaction to succeed. That’s why email security should be at the very top of your business’ concerns.
So why do cybercriminals use emails as their weapon of choice? What are the top cyberthreats making their way into your inbox every day? And how you can launch a robust counterattack of your own?
The Art of Cyber Deception
Psychology plays a larger role in cyberattacks than you might think. Cybercriminals are hitting their targets by deceiving you and making you act irresponsibly, it's called social engineering. And in the midst of the COVID chaos, it's been more successful than ever before. Hackers are constantly developing and deploying sophisticated social engineering tactics to fool unassuming recipients. “They quickly adapt and keep the number of targeted users low. This makes it really hard to detect,” explained Elie Bursztein, (Leader Google’s anti-abuse research team), from observations of how attackers have been updating their designs to make them more efficient.
Cybercrime is steadily evolving to match advancements in technology. Being overly confident or falsely confident about your defenses is certainly not a viable stance anymore. It’s time to adopt a proactive approach to security rather than a reactive one to counter this deception.
Cyberthreats That Invade Your Inbox Routinely
Before we get into building a formidable defense against email attacks, let’s take a look at the top cyberthreats that frequently make their way into your inbox and wreak havoc.
Phishing and Spoofing and Identity Fraud, Oh My!
Phishing involves hackers deploying various social engineering tactics to tempt users into clicking on malicious links and unwittingly giving up confidential information, such as user credentials. Hackers invest a tremendous amount of effort into assuming the identity of a trusted source, making sure that it is YOU who lets them into the system. Once they’re in, they can either install malware on your network’s systems, access and misuse sensitive data, or simply lock your systems and demand a hefty ransom.
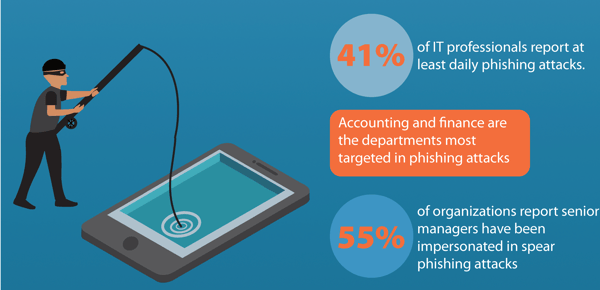
Data suggests that this menace is only growing stronger. Verizon’s 2020 Data Breach Investigation Report stated that 22 percent of all breaches in 2020 involved phishing. The fact that even well-informed users fall prey to such attacks adds to this conundrum. In a study conducted by BullPhish ID, it was observed that 18.6 percent of users that clicked on simulated phishing campaigns demonstrated a willingness to submit credentials or requested data.
Business Email Compromise
How does a business email compromise (BEC) scam unfold? In a BEC attack, the hacker infiltrates your business email account to impersonate employees or any of your organization’s important leaders with intent to defraud your company and its stakeholders into sending money or sharing sensitive data. Spear phishing works in a similar fashion wherein the attacker dupes the user by creating a façade that the malicious email originated from a trusted source.
A GreatHorn report stated that BEC attacks soared by nearly 100 percent in 2019. If you want to get a fair idea about the damage a BEC scam can do to your business, take a minute and think of the massive financial and reputational loss your business would suffer if an attacker impersonates you and carries out fraudulent activities in your name.
Account Takeover
Taking identity impersonation one step further, account takeovers exploit your compromised user credentials to target both your business’ and your financial stability and reputation. Cybercriminals can go to the extent of accessing other accounts, including bank accounts and financial statements, to carry out fraudulent transactions. The 2020 Global Identity and Fraud Report by Experian revealed that 57 percent of enterprises reported higher fraud losses due to account takeovers.
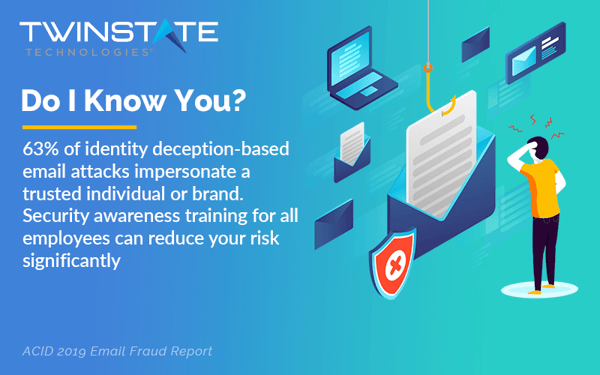
To put it simply, the attacker will not just target your business, but utilize it as a gateway to also exploit your customer data.
Ransomware
A ransomware attack happens when an attacker invades your network’s security, encrypts your data making it unreadable and unusable to you, and demands a large ransom for the restoration of that data. Imagine your business coming to a complete halt until you pay the demanded ransom. Not a good sight by any means! To put this into perspective, in Q2 2020, average ransom demands were pegged at $178,254, which was 60% higher than in Q1 2020 and a whopping 432% higher than in Q3 2019 ($41,198). And these costs can quickly spiral out of control. Just look at the city of Atlanta, they were infected with ransomware and were facing a $52,000 ransom demand but they wound up paying a whopping $700,000 to recover.
To add to the chaos that is 2020, within the last year, there has been switch up in the behavior of Ransomware hits. These cybercriminals have switched tactics and now claim to be EXFILTRATING COPIES of business data BEFORE encrypting it! They are then using additional blackmail threats of exposing the data if an additional ransom demand is not paid.
Malware and Viruses
While the terms are often used interchangeably, malware and viruses differ on technical grounds. Malware refers to any type of malicious software, irrespective of how it works, but a virus is a specific type of malware that self-replicates after entering other programs. Nonetheless, both pose an enormous threat to your business’ IT environment.
CSO Online revealed that 92 percent of all malware is delivered via email and that’s why we’ve included it on our list here. As mentioned before, it only takes one little click for an attacker to gain access to your network’s systems and plant malware or a virus.
Insider Threats and the Human Element
Insider threats are posed by individuals within your organization or related to it, such as current or former staff, suppliers and partners. Acting out of ignorance or out of malice, they can easily let someone into your system, leaving all your sensitive data exposed. According to Verizon in their 2020 Data Breach Investigation Report, over one-third of data breaches worldwide involved inside actors.
An Egress study revealed that 31 percent of employees have mistakenly sent an email containing sensitive data to the wrong person. While your confidence in your employees is well-founded and justified, when it comes to cybersecurity we have to account that to err is human.
Misconfigurations
Last but certainly not the least damaging, misconfigurations in your email platform can expose your network to many threats. For example, it could allow the sending of emails without authentication. This happened not too long ago to a local Plattsburgh, NY organization. Hackers sent out a corrupted email to an organizations mailing list. For those that had email protection in place, the email was recognized as malicious and put into a quarantine mailbox (a win for email protection). Where the protection failed, though, was when a user released the email from their quarantine, allowing the email to do it's dirty work. This is a great illustration of how defense in depth is the best and only way to protect your organization from cybercrime. The email protection did it's work, but the human caused it to fail. In order to prevent this, cybersecurity awareness training is a necessary tool to aid to your security stack.
Engage All Your Defenses
A cyberattack takes place almost every 39 seconds (or approximately 2,240 times a day, as per the University of Maryland). That’s exactly why the time to upgrade your email security is NOW. Your business needs to get on the offensive with a two-pronged approach – implementing the best cybersecurity solutions and providing your employees with extensive security awareness training. Now is the time to implement preventative solutions for endpoint security and backups, identity and access management, automated phishing defense, Dark Web monitoring and security awareness training.
While a 100 percent fail-safe approach to cybersecurity isn’t a reality just yet, Twinstate can certainly walk you through best practices that will put you in strong position for the future. If you have any questions, comments, or feedback reach out to us at 


