You’ve likely seen the headlines recently about ransomware attacks crippling Colonial Pipeline and causing gas shortages on the east coast. These ransomware cyber attacks are becoming more frequent and more lucrative for criminals. Companies have lost hundreds of billions of dollars from these attacks in just the past few years, and they are only becoming more prevalent.
The ransomware threat is not new. It has been around since the late ’80s with the first strain originating on floppy disks and targeting medical researchers at the World Health Organization. However, it is just now becoming a growing concern across the country after that massive Russian cyberattack on Colonial Pipeline made its effects felt nationwide. So what exactly is ransomware and what can you do to protect your company?
Ransomware Explained:
“Ransomware -- it sounds like a fashion line for casual, yet elegant kidnappers.”
- Trevor Noah, The Daily Show
Ransomware is a form of digital extortion. These attacks refer to the deployment of malware -- malicious software -- onto a corporate environment. Once installed, ransomware encrypts all of the data in the environment, locking it from use indefinitely unless it is decrypted. All of the files and systems that rely on those files are rendered completely useless and operations are brought to a halt. Many companies are also blackmailed by the hackers who threaten to leak any of the sensitive information they've touched on your network.
Only the hackers will be able to decrypt that data using a key that only they have. These hackers often demand the original owners pay a digital ransom using a cryptocurrency like Bitcoin in exchange for the decryption key. Many companies do choose to pay the ransom, but is it worth the price?
Ransomware Infections: Should You Pay the Ransom?
Paying the ransom is often a roll of the dice and the hackers will not follow through with their promise to unlock your files. As was the case with Colonial Pipeline. After paying the ransom, estimated to be in the millions, the hackers never provided a usable decryption key to the pipeline. Ultimately, the company had to rely on its backup instances to get back on its feet.
The FBI warns against paying these extortion fees. However, many companies panic and pay the ransom with varying results. The one certainty about paying a ransom is that it encourages the hackers to keep deploying ransomware. A report by the Center for Strategic and International Studies and McAfee estimated the worldwide cost of cybercrime at almost one trillion dollars between 2018 and 2020. Sadly those payments encourage these criminals to continue their targeted attacks.
Victims of Ransomware: Most Targeted industries
Critical infrastructure providers, big and small, from pipelines and manufacturers to healthcare and local governments are often targeted by hackers demanding the steepest ransoms.
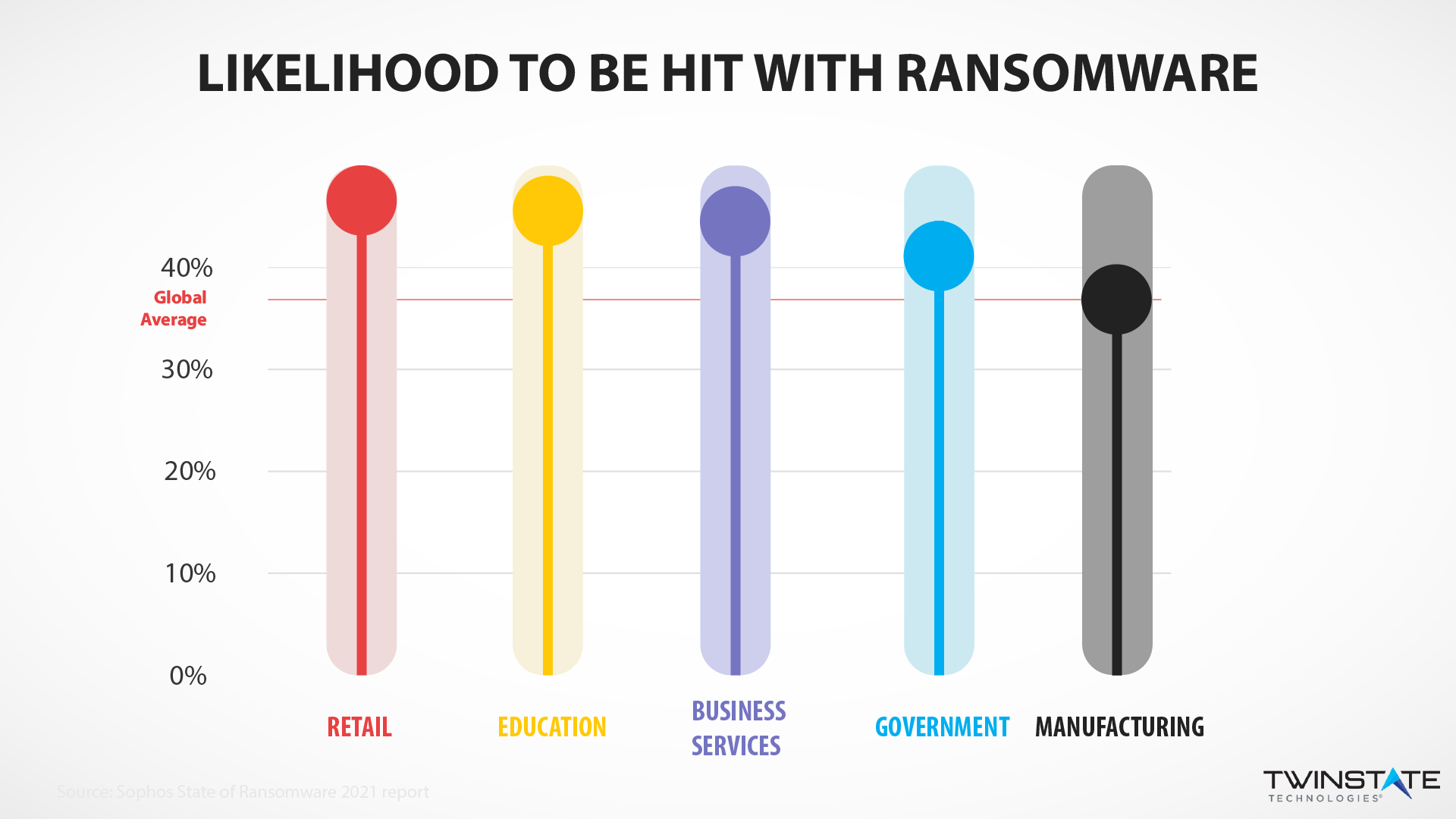
But make no mistake, ransomware is a crime of opportunity. Any group with an easy to exploit vulnerability will be targeted with ransomware. School districts, hospitals, and businesses small and large are frequently attacked with ransomware.
Anatomy of an Attack: How Does Ransomware Get on Your Network?
Ransomware attacks often happen from phishing campaigns (like emails with malware hidden in a suspicious link), remote desktop protocol vulnerabilities (hackers gain access to a computer or network over the internet), and software vulnerabilities (hackers exploit security weaknesses and widely used software to access people's data).

It's common for these attacks to originate from organized crime syndicates that work out of Russia, North Korea, China, and Iran. This makes it challenging for the United States to bring these criminals to justice or penalize them.
Ransomware Protection: Cybersecurity is a Team Sport
Industry experts say that updating computer security infrastructure is critical; many organizations that operate on legacy technologies are highly vulnerable to attacks. Some elected officials have advocated legislation and the U.S. Chamber of Commerce is lobbying the Biden Administration to take action such as requiring companies to share information with the government when an attack happens.
Ultimately, it is your responsibility to act and protect your company. Ransomware attacks are often crimes of opportunity, infecting victims who have easily exploitable weaknesses in their defenses. Poor cyber hygiene puts a massive target on your back. The Cybersecurity and Infrastructure Security Agency (CISA) recommends organizations implement several layers of practices to reduce their risks, a practice known as defense in depth. Some of the top recommendations to prevent ransomware include:
- Keeping software and firmware up to date
- Regularly patching security flaws (something managed patching services can help with)
- Run a network vulnerability scan to assess your security standing
- Create a cybersecurity culture through employee cyber awareness training
- Inspect emails for impersonation and malicious links with an email security solution
Twinstate Technologies is the leading IT Security provider in Upstate New York, and New England. If you have any questions about ransomware and your security posture, please reach out to us and we would be happy to consult with you.



COMMENTS