Security researchers at Lookout have discovered a sophisticated, new phishing campaign that is targeting Verizon Wireless customers on their mobile devices. This phishing kit is different from other phishing kits and demonstrates a new level of sophistication in two ways.
First, phishing kits that target mobile devices aren't very common. The Verizon phishing scam shows that cyber criminals are evolving their hacking methods to align with shifting technology trends. As more workers rely on mobile devices at home and at work, it is likely that we will start to see an uptick in phishing campaigns optimized to hit mobile devices.
The hackers behind this campaign also displayed knowledge about Verizon's infrastructure which indicated they did a significant amount of research before launching their attack. Their familiarity with Verizon's operations sets them apart from traditional phishing campaigns.
The attackers hide the phishing link in a message that appears to come from Verizon Customer Support. When the link is clicked, the user is taken to a website that is a convincing spoof of the Verizon app.
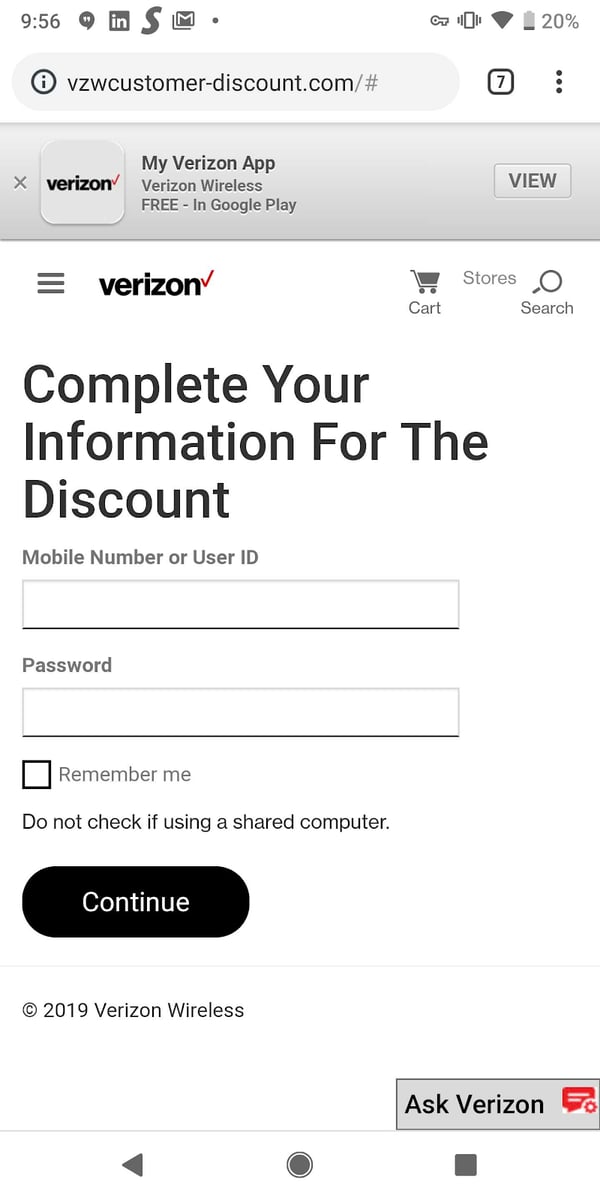
Attacks on mobile devices are proving to be highly effective because most mobile devices lack even basic security. As hackers increasingly target mobile devices in their attacks, it is critical that organizations understand their risks and adopt a security approach that addresses their vulnerabilities.
3 Ways to Minimize Your Organization's Phishing Risk:
1. Email Security Software
Email has made communication efficient and convenient for everyone, including hackers. Email has become the medium of choice for phishing and malware distribution.
2. Dark Web Monitoring
The goal of a phishing campaign is to trick a user into handing over valuable information -- social security numbers, passwords, account numbers, DOB, etc. The individual(s) behind these campaigns then sell this information to other criminal on the dark web.
Dark web monitoring solutions keep you protected from exploitation by constantly scanning dark web marketplaces for your information. When your information is detected, you will be immediately alerted and given instructions for remediation.
3. Awareness Training
Your users are the most important component of your organizations security. You can have the best security solution in place , but it takes just one of your employees connecting to your network with an infected mobile device to circumvent every ounce of security you have in place.
Training your employees to recognize and understand the latest cyber threats will help your organization prevent falling victim to attacks.
