The OSI Model is well-known by IT professionals as a helpful framework when it comes to troubleshooting technology. As a small business owner, you're likely wondering how the OSI model could possibly be of use to you. Well it has a major impact on your employees, particularly at layer 8 of the model. Let's break down how Twinstate Technologies secures layer eight, our employees, at our Plattsburgh, NY office location. But first, what do we really mean by layer eight in the OSI model?
What is LayerEight in the OSI Model?
Layer eight is often referred to as the "employee element" and is considered an add-on layer to the traditional OSI model. The actual OSI model contains just seven layers, providing a visual representation and conceptual framework for the functions of a computer or telecommunications network.
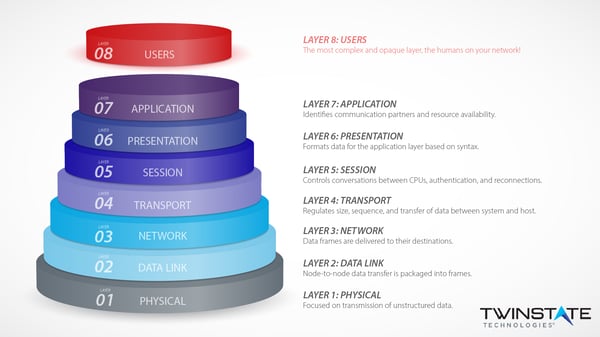
Layer 8 is a conceptual extension to OSI model that was created to cover the most complex element of a network, the end-user. End-users have a significant impact on the integrity of the networks they use. Whether it be through be through downloading a virus, using compromised credentials, or simple human error -- network users actually pose a significant and unpredictable security threat.
How do managed service providers help the end-user in layer eight?
Managed service providers (MSPs) or an outsourced IT department can help companies at all levels of the OSI model, but their value really applies to layer eight, a company's employees. If you're not familiar, managed services take care of all the hassle that comes with business technology. From routine maintenance and automatic patching to proactive monitoring, training, and help desk support, your technology remains up to date because it's consistently taken care of by an MSP. Basically, when it comes to information technology, managed services make your business more efficient, secure, and cutting-edge.

So, how does that all affect an end-user? Read below to learn how Twinstate Technologies applies our managed services to benefit layer eight at our company.
Five ways your business employees get the most from our managed IT services:
Routine Maintenance
Routine maintenance of our network infrastructure and workstations keeps everyone and everything working smoothly in our Plattsburgh, NY branch. In life, and in IT in particular, the longer you put off solving a problem the harder it gets to solve. By regularly maintaining and upgrading the technology our team relies on, we prevent the many headaches that pop up just from using dated tech and the headaches that do arise are much easier to troubleshoot. Automatic Patching
Timely application of patching is essential to business security as the Microsoft Exchange Email Server Breach has just demonstrated. As a part of Twinstate's managed services and routine maintenance, our IT techs have automated the application of patches to our employees workstations. Whether it be the latest patch from Microsoft or a patch from a third-party vendor, our team is on top of it.Proactive Monitoring
Cyber crime doesn't happen out of nowhere, there are often telltale signs leading up to an incident. When those signs are identified proactively, most of the time a breach can be prevented. Twinstate's cybersecurity team in Plattsburgh has 24x7 monitoring established for our employees. We are constantly monitoring the dark web for signs of compromised credentials and inspecting network traffic to prevent intrusive and damaging traffic. Employee Awareness Training
Human error is one of the leading causes of data breach, not the basement dwelling hackers that we often imagine. Simple mistakes made by employees -- like accidental file deletion, data corruption, or downloading malicious software -- can cost business massive amounts each year. Employee awareness training can prevent these incidents for just a few dollars a month.
At Twinstate Technologies every one of our employees is enrolled in regular cyber awareness training sessions to minimize our biggest risk, human error. This might sound like a giant undertaking that's expensive and time-wasting, but it's really the opposite. Effective awareness training needs to be kept brief and conducted frequently. That's why we use micro-learning videos to teach our team. It takes just 10 minutes a month and our team can engage in the sessions on their own schedule. Our Information Security Team in Plattsburgh regularly create and send mock phishing emails as well to our internal users to test their knowledge retention.
IT Support
During the COVID-19 restrictions, our Plattsburgh office has been operating in hybrid-model with some employees in the office and many more of our staff working from home. In this environment, having remote support available to our crew has been essential. IT support that was delivered remotely helps our team troubleshoot and resolve issues much more quickly and safely. For our managed service clients, IT Support is available 24x7, 365. Our team is always here for you, we don't get sick and we never take vacation.Layer eight is one of the most challenging layers of the OSI model to handle but managed service providers can really help your small business keep your users secure and efficient. If you think managed services are right for you, let's talk.



COMMENTS