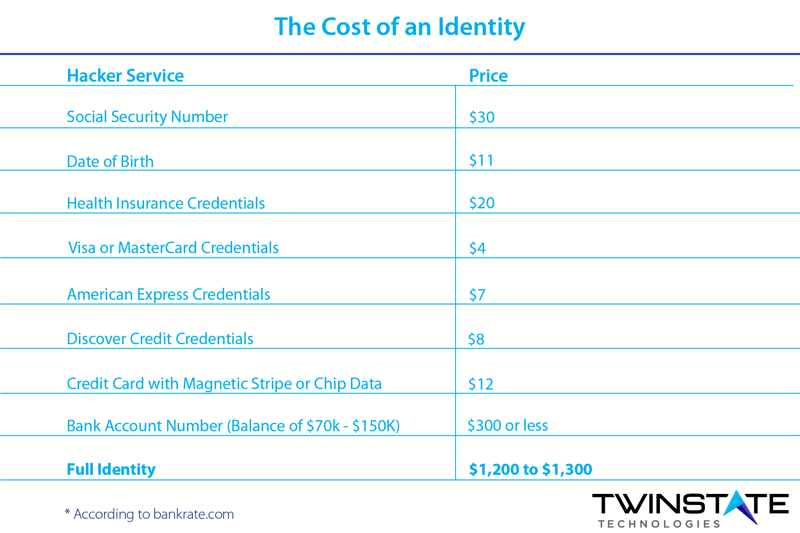
CPA’s and bookkeepers are entrusted with confidential information by their clients. In the wrong hands, this information can be of value to someone else. It has been estimated that a full online identity can bring in $1,300 on the dark web, the more pieces of your clients' information, the more value to crooks. So, even if you think that you are too small of a target for someone to steal from, what you hold is of interest to evil doers and it can be used to generate more income for the cheats and thieves that use it.
Here are a few pointers to consider to safeguard your clients' information when it is in your custody.
1. When handling client financial information, ensure only those people that absolutely need to view the documents have access to those documents. Take steps to lock the files so only authorized staff can view and handle the information. Over the past decade, we have transitioned to computer spreadsheets and files stored on servers. Identity theft has become a billion-dollar business for cybercriminals, with new regulations penalizing firms that miss handle or store the information improperly. Below are a few tips to better protect your client’s information.
2. Make sure that you have performed all of your authentic security updates on software you use and have effective antivirus and Managed Security from a trustworthy service provider such as Twinstate Technologies®, whose endpoint protection includes an effective, machine learning capability, such as Sophos Intercept X. This level of antivirus protects against ransomware and other types of malware. Ransomware will encrypt all of your files it has access to PLUS can also send the contents off to be sold. By getting this infection it is both expensive, embarrassing and possibly catastrophic. Bad Cats can also watch what you are doing and send that information off to their servers to be sold by use of Key Loggers, like the song, “every step you take, every move you make, I’ll be watching you…”, that’s what the creeps do.
3. Email Encryption: When you must send to and receive information from your client or vendors to assist the best practice is to use email encryption. Email encryption has come a long way and is now simple, effective and affordable. Sending an encrypted email can be accomplished with the click of a button. Only the recipient of the email will have permissions to open the email. The client simply replies to the email and the message stays encrypted. This provides a safe and effortless way to transfer sensitive information without the worry of prying eyes. If you email is not encrypted you should be aware that people can “view” the contents anywhere that email travels through servers, ISP’s, etc.
4.File and Folder Encryption: By encrypting files you basically obfuscate the information. If crooks do get access to the files, they won’t be able to read them anyway. Encryption of files and folders also helps to prevent accidental disclosure and mishandling. File and folder encryption is a very effortless process to implement that adds another level of protection for your client’s most sensitive information.
5.Limit Access to the Information: If you are not ready for encryption you can also gain some level of security by limiting access to who can view the information. This can be done with file and folder permissions.
6. Perimeter Protection: Many firewalls are not effective in defending against today's adversaries. Perimeter Protection provides small businesses with big business technologies and security solutions. Limiting websites your team can get to can limit your risk of malware infection. Limiting malware infections reduces your risk of your or your clients’ data getting onto the Dark Web and available for sale. Perimeter Protect also provides protection by blocking many bad actors from getting into your network in the first place. And with awful stuff like Ransomware, when in your network the malware connects back to the command and control (c2) mothership of sorts…the Perimeter Protect will stop attempts for it to connect to known bad IP addresses. Perimeter Protect also has ongoing support services to keep it up to date without you ever having to touch it or worry. All watched by a team of Information security professionals.
7. Back Up All of Your Data: It is essential to have absolutely functioning backups. How do you know if they work? Make certain you test them before you have a need for them. Back up options are many so rely on a trusted MSSP to really look at what works best for your firm and protects your data and customers' data if things get ugly.
There are other things that you can do to safeguard your clients' information but these are a few steps to start on the right path that your service provider would be proud of!

