Social engineering is essentially the hacking of a human. These exploits have a long history that predates the rise of the internet and even computers. They remain relevant in today's tech-driven world because it is much easier to hack a human than it is to hack into software or hardware.
This post dives into what social engineering is, the different types of social engineering, some ways to recognize a social engineering attack, and tips to avoid falling victim to social engineering scams.
What is Social Engineering?
Social Engineering exploits humans inclination towards trust in order to manipulate people into handing over specific information. This done in a number of ways including:
One of the most famous social engineering attacks took place sometime around 1200 B.C. when Ulysses, the commander of the Greek army, concocted the famous Trojan Horse scam. He managed to trick the Trojans into believing that the Greek army had retreated back to Greece and that they'd left a giant wooden horse as a peace offering to the goddess Athena. The Trojans had no idea that the Greek army was hiding inside the horse until they'd brought it inside the gates of their city.
Modern social engineers follow a similar approach today. They will place infected USB drives around organizations parking lots in hopes of baiting an employee into bringing the USB drive inside the gates of their organization.
Types of Social Engineering Attacks
Phishing
Phishing emails will be sent that look like they're coming from a trustworthy source, like a business or a colleague that the victim frequently interacts with. The victim is often prompted to click a link and sign in to one of their web accounts. When clicked, the link will take them to a fake website that has been set up to look identical to the website the victim thinks they're visiting. When the victim gets to the spoofed website and logs in, they've just hand delivered their login information to the attacker.
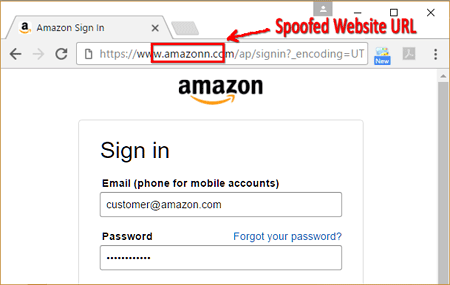
This example shows how convincing a spoofed website can be. It looks just like the Amazon sign in page and the only giveaway that this is a phishing attempt is the extra "n" in the URL.
Lately, we've been seeing complex phishing websites that are complete with a security certificate, making it more difficult to distinguish between a legitimate site and a fraud.
Test Your Phishing Knowledge
Business Email Compromise
In a business email compromise, an attacker will take over someone's email account, either by purchasing the login credentials on the dark web, cracking the password, or phishing the information.
The attacker will use this account to begin sending emails to individuals on the accounts contact list. These emails might contain links that will spread malware when clicked. This is particularly concerning because users are highly likely to click a link that they think was sent to them by a friend or coworker.
If the attacker compromises a CEO's email account then they will often send emails to the finance department directing them to make an urgent money transfer to a specific bank account. These attacks are often successful by instilling a sense of urgency in the recipient so that they don't think twice about what they're doing.
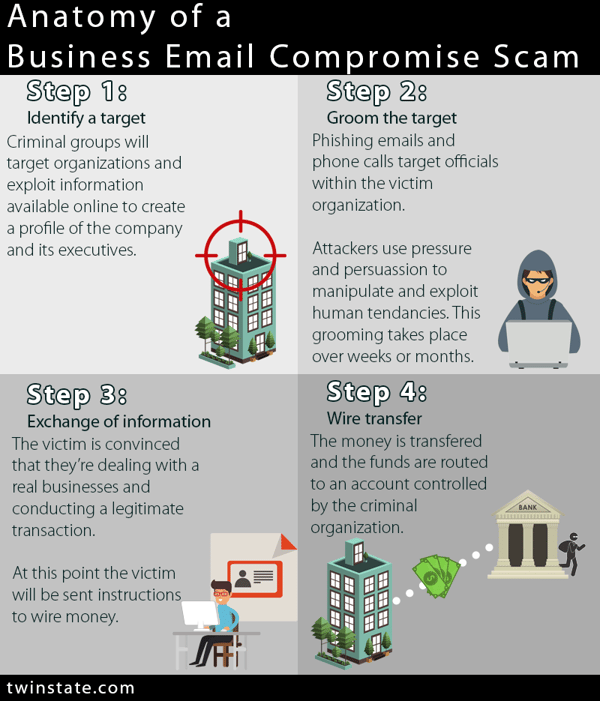
Other times the attacker compromises a vendors email account and will send payment requests to your organization. These attackers will study your payment processes in order to craft contextually relevant believable messages. By appearing as a vendor that your company regularly does business with, these attacks are successful by exploiting the trust that is built up from ongoing business relationships.
Vishing
Vishing, or “voice phishing,” is the telephone version of phishing. As with phishing, a vishing attacker will try to make themselves appear as an authority that you’re familiar with like a bank or government agency.
Most vishing scams originate outside of the United States, but by using caller ID spoofing, the attacker can make it appear as if their phone call is coming from a legitimate local source. Spoofing earns the trust of the victim and compels them to answer the call and believe the caller is whom they claim to be.
A skilled visher can scam individuals and institutions alike.
There are many examples of vishers gaining access to target accounts in under 2 minutes, such as the example below:
Pretexting
An attacker will create a fake identity for their self and present a made-up scenario to their victim to get the victim to hand over valuable information to the attacker.
For example, the attacker may inform the target victim that they are the beneficiary of a will belonging to a long-lost Aunt who recently passed away. The attacker will tell the victim they need to authenticate their identity by providing a social security number to the attacker.
An attacker might disguise their self as an external IT auditor and manipulate an organization security staff into divulging privileged information.
SMiShing
Where phishing uses email and vishing uses phone calls, SMiShing uses text messages to exploit a victim. This emerging trend is particularly alarming due to people's inclination to trust a text message more than an email. While many people are aware of the risks associated with clicking unknown links in an email, that same awareness hasn’t spread to links in text messages.
A typical SMiShing message will tell you that you are going to be charged daily for a made-up service. A link is provided to opt out of the service and avoid the charges and asks for your personal information to submit your preference. Ignore this message unless you did indeed sign up for a service that you would like to cancel.
Another tell-tale sign of a SMiShing message is if it comes from a “5000” phone number.
How to Recognize a Social Engineering Scam
- Asking for immediate assistance
- Asking you to donate to a charitable cause
- Asking you to "verify" your information
- Responding to a question you didn't ask
Asking for immediate assistance
Social engineers will use language that instills a sense of urgency in their victims to try to pressure the victim to rush into action without thinking about it.
If someone asks you to make an urgent wire transfer, this is a sure sign that you should slow down and ensure that the transaction you'll be conducting is legitimate.
Asking you to donate to a charitable cause
Social engineers will exploit our generosity with phony requests for donations to charitable causes which includes payment instructions on how to send money to the hacker.
By researching you on social media, a social engineer can figure out what charitable causes, disaster relief efforts, or political campaigns that you are likely to support. They will use this information to craft messages aligned with your ideals.
Asking you to "verify" your information
Another approach social engineers will take is presenting a problem that can only be resolved by you verifying your information. Included in their message will be a link that brings you to a form to provide your information.
These messages and forms can look legitimate with the right logos and branding, which can lull you into believing the sender and the message are legitimate.
Responding to a question you didn't ask
Social engineers will pose as s customer service agent from a company you do business with and send you a message "responding" to a request for help. Though you never sent a request for help, you might decide that since you already have a rep contacting you, this would be an opportune time to receive support for an issue you've been experiencing.
Inevitably the attacker will request specific information from you to "authenticate your identity." In reality, they're just stealing your information.
How to Prevent Social Engineering?
- Identify your valuables
- Verify Identities
- Slow down
- Verify links before clicking
- Education
- Email protection software
Implementing each layer of a defense in depth strategy is an excellent place to start protecting your organization from all cyber threats, including social engineering attacks. To further protect yourself, below is a list of five tips to prevent social engineering.
Identify Your "Crown Jewels"
Knowing what information you have that is valuable to a hacker helps you to see what you need to protect from a hacker. Your Crown Jewels will be different for your organization than it is for others, so doing this exercise yourself is important. There is no "one size fits all."
Verify Identities
Make sure that you're actually dealing with whom they claim to be. Email hijacking happens every day, putting legitimate email accounts under the control of criminals.
If you receive a request via email that's out of the ordinary but it's coming from an email address that you're familiar with you should call the sender to confirm if they did indeed send you the message in question.
Slow Down
Social engineers try to instill a sense of urgency in their victims so that they rush to action and overlook potential red flags that they might be dealing with someone who is not legitimate.
Slow down and evaluate the situation with a clear mind before rushing into anything. If the transaction is legitimate, then the person on the other side will be understanding and patient with you doing your due diligence.
Verify Links Before Clicking
If you receive a shortened link, such as a bit.ly link, it may be covering up a malicious URL. To test the link without clicking it, you can use a link expander. The search engine DuckDuckGo has a link expander built right into it so you can see what's behind that short URL.
Education
Preventing social engineering starts with generating knowledge and awareness around the problem. If your users aren't aware of social engineering threats, you can't expect them to exercise the necessary caution to keep your organization protected.
Secure Email Software
Protect against social‐engineering attacks that attempt to impersonate your executives, staff, partners, and well-known internet brands to fraudulently extract money or data from your unsuspecting users
Email protection software will examine messages coming into your inbox for signs of malware, malicious intent, and impersonation attempts and will stop them from getting into your inbox in the first place.
To prevent clicking of malicious links, URL protection software and applications help protecting every click your user makes on every device they use.




COMMENTS